Blockchain Cargo Container Global Aggregation
The 2021 global supply chain log jam and its continuing congestion and snarls reveal a critical need for a method to locate and aggregate empty available cargo containers worldwide. That method must be easily deployable and managed by its end users. This paper presents a Blockchain-based solution for finding available cargo containers across dynamic global ecosystems and generating trusted real-time contracts between aggregators and container providers.
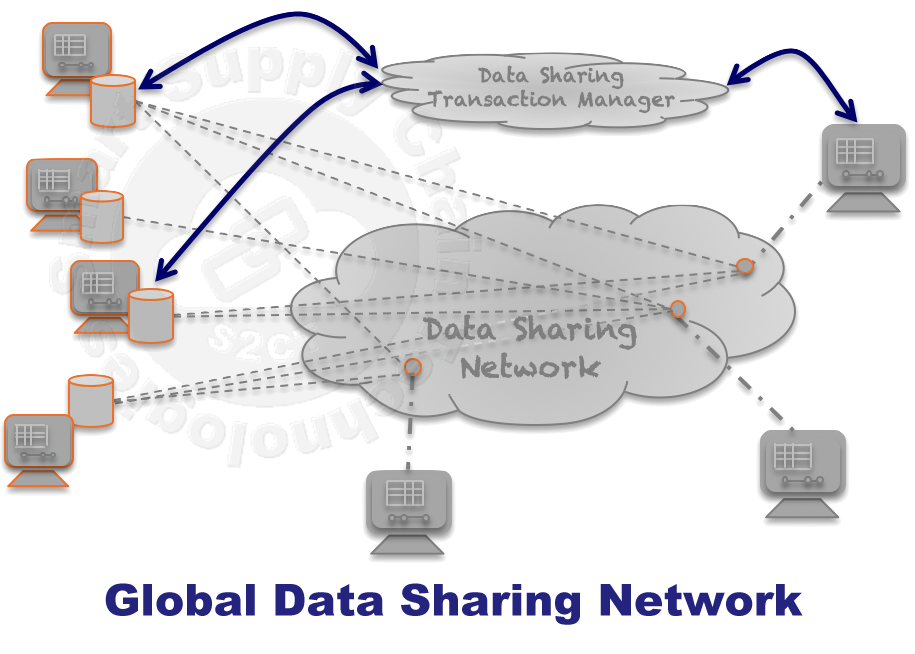 The Blockchain Cargo Container Global Aggregation model described here is based on a Data Sharing Network concept and architecture, originally developed to track and monitor cargo moving through the global supply chain in 2006. Fundamentally this is a highly secure method for business associates to collaborate and share Private Data. Here container providers are sharing their confidential inventory data with prospective customers trying to aggregate container inventories to meet their real-time supply chain requirements. The network is self-annealing; aggregators and providers dynamically decide what data they will share and with who. Self-annealing is a term intended to suggest that sharing Private Data is driven by the value reaped by the sharer. This is what is known as a permission-based Blockchain today.
The Blockchain Cargo Container Global Aggregation model described here is based on a Data Sharing Network concept and architecture, originally developed to track and monitor cargo moving through the global supply chain in 2006. Fundamentally this is a highly secure method for business associates to collaborate and share Private Data. Here container providers are sharing their confidential inventory data with prospective customers trying to aggregate container inventories to meet their real-time supply chain requirements. The network is self-annealing; aggregators and providers dynamically decide what data they will share and with who. Self-annealing is a term intended to suggest that sharing Private Data is driven by the value reaped by the sharer. This is what is known as a permission-based Blockchain today.
An ecosystem is a group of business-related parties, or companies,  that have each installed Data Sharing Network Software in their computing/data environments to selectively and securely share Private Data.
that have each installed Data Sharing Network Software in their computing/data environments to selectively and securely share Private Data.
Computing/data environment means anywhere in their computing environment where the Data Sharing Network software can access their ecosystem Relevant Data and share it, over the internet, with other ecosystem associates. A desktop computer connected over the internet to cloud storage and ecosystem members is a simple example.
Ecosystems are dynamic in that participants can come and go, change what data they share with specific ecosystem associates, and arbitrarily grant and remove data sharing permissions with specific ecosystem parties or the entire ecosystem at any time, for any reason. Ecosystem associates are motivated to remain in and contribute to ecosystems based simply on the value proposition for their businesses.
This Blockchain model has evolved since its original demonstration in 2006 to include techniques developed and driven by the advent of cryptocurrencies. Every block in the Blockchain is asymmetrically encrypted, requires multiple passcodes to decrypt, is distributed in its encrypted form, is immutable using hash methods, and has many disjoint redundant copies across the ecosystem to ensure its integrity. See Smart Supply Chain Technologies' Data Security in the Global Supply Chain White Paper for our data security perspective(2). Below is a simple hash-fingerprint example illustrating how it's used to detect if the contents of a Blockchain block have been altered.

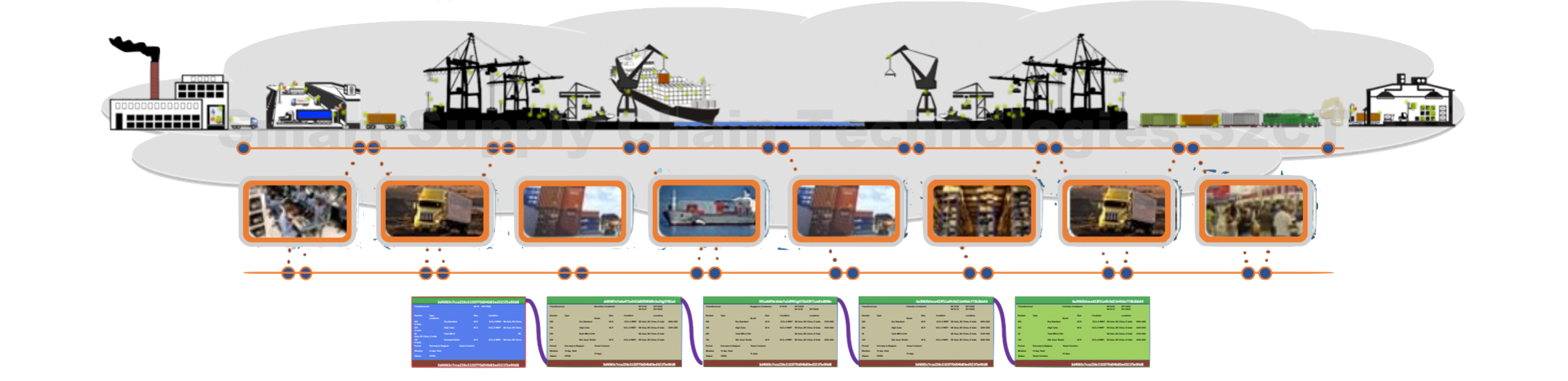
An ecosystem search for available containers begins when an aggregator creates the first Blockchain block. This first block, called a Transaction Block, gets distributed in its encrypted form to every node in the ecosystem.  Transaction Blocks describe the details of what the aggregator is searching the ecosystem for. Every Transaction Block spawns at least one Blockchain with at least one additional no-reply block but typically results in multiple Blockchains with blocks from many different potential providers. Transaction Blocks are essentially the first entry in a virtual ledger expecting to be followed by blocks from responding providers. The virtual ledger is a common shared ledger where every node has a copy of every block in every Blockchain created by the ecosystem. Separately the aggregator, using the Data Sharing Network Transaction Manager(1), sends the second private encryption key to ecosystem members that have the aggregator's permission to view the contents of the Transaction Block. Ecosystem nodes that receive the second private key can verify the Transaction Block's hash fingerprint, read its contents, and confidently respond to the search.
Transaction Blocks describe the details of what the aggregator is searching the ecosystem for. Every Transaction Block spawns at least one Blockchain with at least one additional no-reply block but typically results in multiple Blockchains with blocks from many different potential providers. Transaction Blocks are essentially the first entry in a virtual ledger expecting to be followed by blocks from responding providers. The virtual ledger is a common shared ledger where every node has a copy of every block in every Blockchain created by the ecosystem. Separately the aggregator, using the Data Sharing Network Transaction Manager(1), sends the second private encryption key to ecosystem members that have the aggregator's permission to view the contents of the Transaction Block. Ecosystem nodes that receive the second private key can verify the Transaction Block's hash fingerprint, read its contents, and confidently respond to the search.
That response will be in the form of an asymmetrically encrypted block sent to every ecosystem node with its reply to the search, its hash fingerprint, and the from-hash fingerprint of the Transaction Block. This distributed Blockchain now has two blocks, the Transaction Block linked to the response block. Again, only the permissioned nodes, here only the aggregator, will be permissioned to decrypt and view the responding block's contents. Responding blocks will contain the details of the container inventories the responder is offering to the aggregator that satisfy some or all of the search criteria.
The Blockchains begin to take shape across the ecosystem. 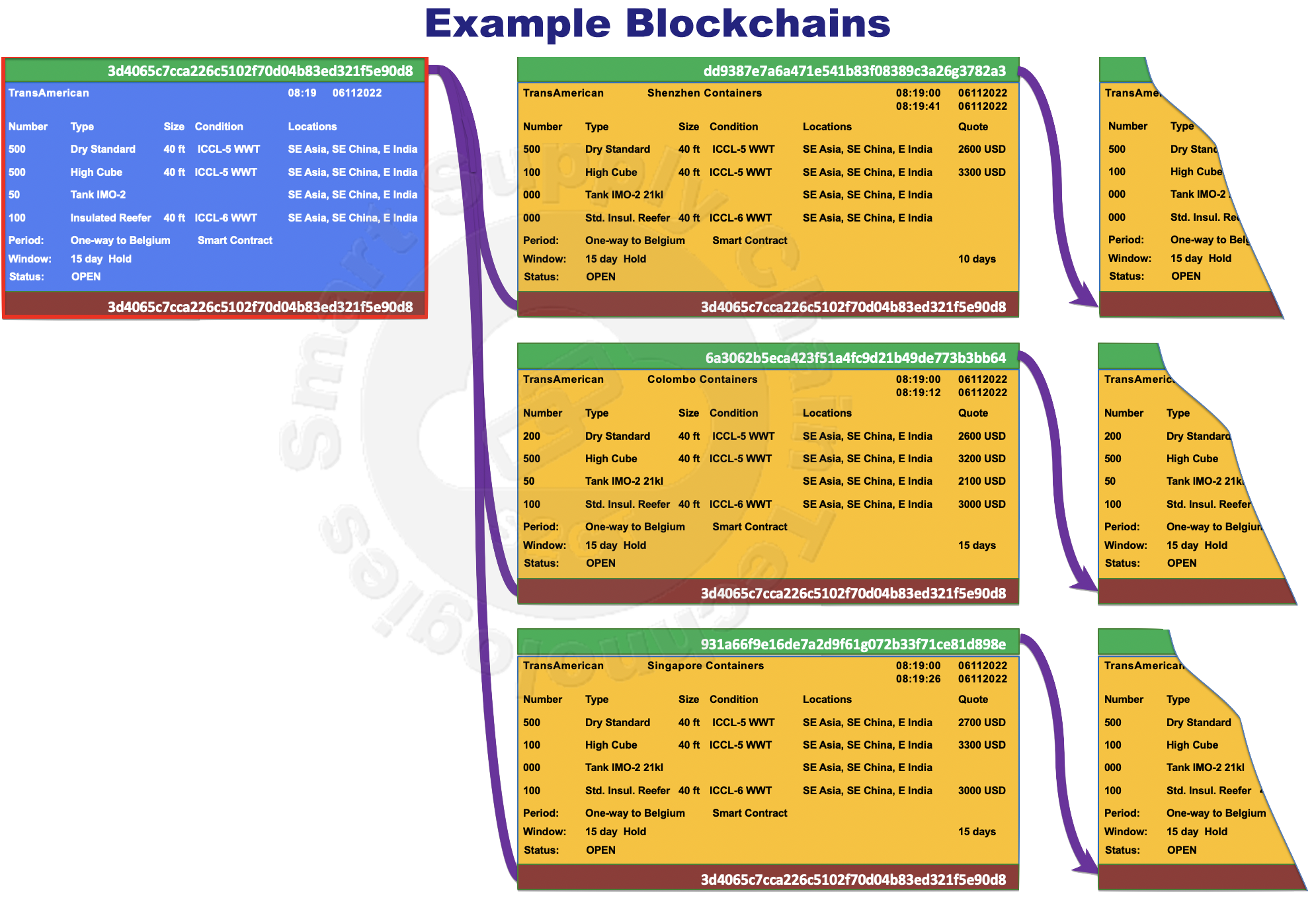 Every ecosystem responder's block has embedded in it its unique hash fingerprint and the same hash From-fingerprint linking them all to the aggregator's Transaction Block. In this manner, each response block creates a new independent Blockchain. Again, only the permissioned ecosystem nodes receive private passcodes ensuring only the aggregator can view the content in responder blocks, not other responders.
Every ecosystem responder's block has embedded in it its unique hash fingerprint and the same hash From-fingerprint linking them all to the aggregator's Transaction Block. In this manner, each response block creates a new independent Blockchain. Again, only the permissioned ecosystem nodes receive private passcodes ensuring only the aggregator can view the content in responder blocks, not other responders.
The Transaction Block must contain all of the necessary information required for ecosystem businesses to meaningfully respond to each aggregator's search specifics, across all kinds of business models: lease, sale, one-way, round-trip, mixed and extended periods, container redistribution, storage, container exchange, etc. The Transaction Block must also make provision for aggregators to provide other details that will be required for the container providers to satisfy in an eventual contract.
To that end, Standard Models for this Relevant Data must be developed within ecosystems that will ensure the precise requirements of the aggregator are clear to potential responding providers. All Blockchain blocks must include a timestamp reflecting the time and date of its addition. Even compromises that might evolve as the process progresses, block to block, must have enough specificity and rigor to be included in an eventual Smart Contract(3) at the end of the Blockchain.
A Standard Model for Relevant Data in a Transaction Block will typically include the specific number of specific types and sizes of containers sought, their required conditions, their desired retrieval locations, desired lease and or purchase terms, required hold-time before retrieval, and anything else that the aggregator specifically requires from the providers. The Transaction Block and resulting Blockchains, illustrated in this paper, are simple examples of an aggregator's search.
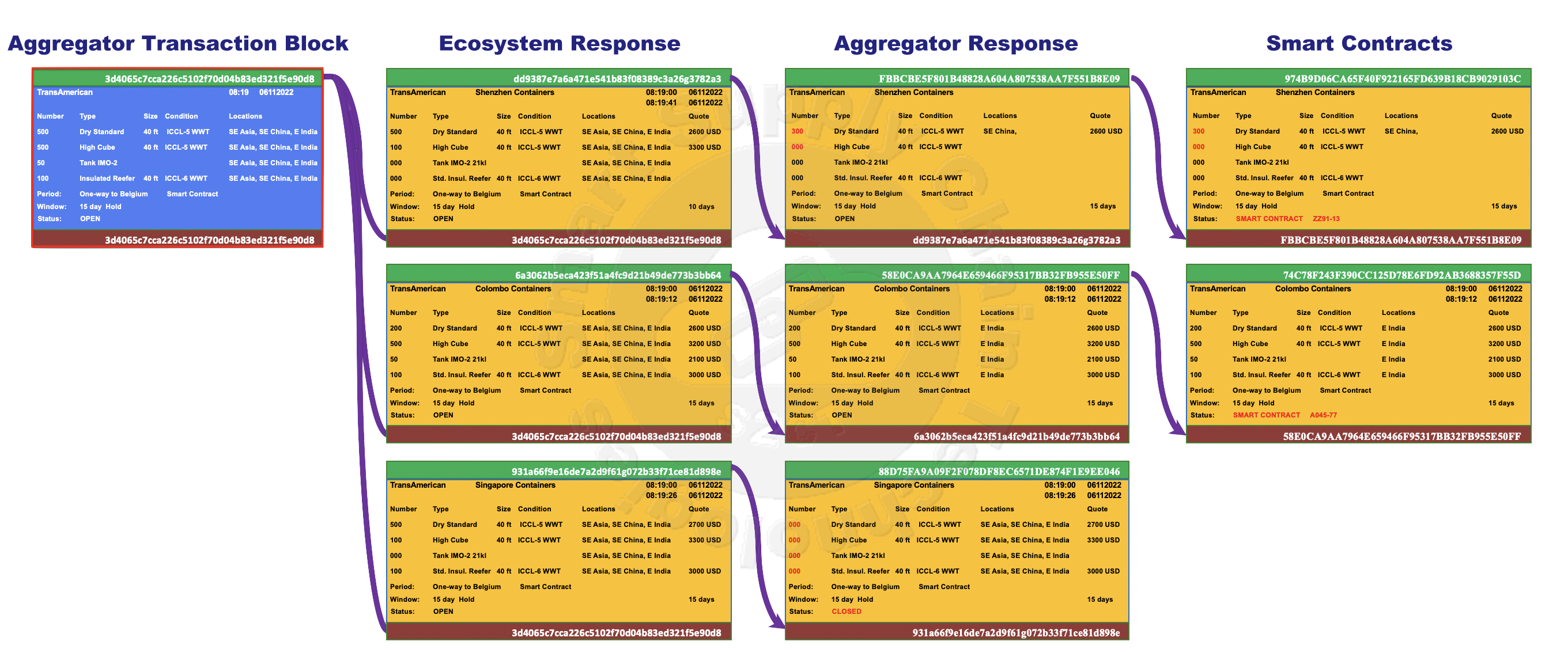
The Blockchains above illustrate three ecosystem provider responses to an aggregator's search. The first Blockchain, stemming from the aggregator's Transaction Block, reflects a response from Shenzhen Containers in a block offering only some of the containers in the search. That response block is followed by a response block from the aggregator partially accepting Shenzhen Containers' offer, highlighted in the illustration with red text. The aggregator and Shenzhen Containers eventually arrive at an agreement, and a Smart Contract block gets added to the Blockchain. Note that only the aggregator and Shenzhen Containers have access to the immutable content within the blocks of their private Blockchain, except the Transaction Block.
The second Blockchain, resulting from a response from Colombo Containers, shows that the aggregator fully accepted Colombo Containers' offer. That second Blockchain also concludes with a Smart Contract reflecting that agreement.
The third Blockchain illustrates the aggregator deciding to reject the offer from Singapore Containers, presumably based on some business rationale, and terminating that Blockchain without a contract. Copies of all three Blockchains are distributed across the ecosystem in their entirety. Every ecosystem node saves an encrypted copy of every ecosystem Blockchain, theoretically stored forever.
Aggregator-initiated Blockchains terminate either as rejected and closed or accepted in a Smart Contract. Smart Contracts won't be elaborated upon here other than to say they are software-generated contracts automatically generated when a specific set of conditions and parameters are satisfied. Smart Contracts share all the attributes described here for Blockchain blocks and maintain the security, privacy, integrity, and reliability underlying all permissioned Blockchains. Smart Contracts can be very powerful and much more than just a contract. IBM's Smart Contract(3)(*) model, for example, not only generates the Blockchain contract but can then manage its entire workflow through fulfillment.
This Blockchain model and methodology provide supply chain constituents with a simple, quick-to-deploy, flexible, cooperative data sharing method to locate, monitor, and aggregate supply chain assets. The model's underlying architecture and software have been successfully demonstrated in a broad range of tracking and monitoring applications since 2006, starting with tracking cargo through the global supply chain(4).
With the widespread availability of the internet, SpaceX Starlink(*), and others, and the acceptance of using the Cloud to store private data, ecosystem data collaboration will become quite diverse. Virtually anything can be tracked and monitored anywhere in the world, from anywhere in the world, with an ever-increasing resolution, by ever-increasing collaborating ecosystem constituents sharing data.
Jim Davis is a principal at Smart Supply Chain Technologies, U.S.A.
Eric Lam is a former Smart Supply Chain Technologies associate, Hong Kong
Maria Gerard G. Prakash is Managing Director, Star of Seas Marine Enterprises, Mumbai, India
(*) All company and product names are trademarks TM or registered ® trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.
References:
(1) The S2CT Dynamic, Secure, Peer-to-Peer, Private Data Sharing Network with Blockchain https://s2ct.tech/whitepaper-data-sharing
(2) Data Security in the Global Supply Chain https://s2ct.tech/whitepaper-data-security-in-global-supply-chain
(3) What are smart contracts on Blockchain? | IBM https://www.ibm.com/topics/smart-contracts
(4) The S2CT Dynamic, Secure, Peer-to-Peer, Private Data Sharing Network with Blockchain https://s2ct.tech/whitepaper-data-sharing
Useful Reference Materials: